Secure Sockets Layer Support (SSL) & Transport Layer Security (TLS)
QWS3270 Secure supports Secure Sockets Layers (SSL). The following section presents a brief introduction to some of the concepts and techniques involved in public-key cryptography and, more specifically, the Secure Sockets Layer (SSL) protocol.
QWS3270 Secure supports SSL 2 and 3 and TLS 1.0, 1.1, and 1.2 (Transport Layer Security), sometimes referred to as SSL version 3.1.
What is SSL?
SSL stands for Secure Sockets Layer. It was developed by Netscape Communications for use between clients and servers.
It layers on top of any reliable transport protocol and can run under application protocols such as HTTP, FTP and Telnet.
It is secure, fast and easily adapted to other web protocols.
It uses public key cryptography. For more details on cryptography look at the following section.
See below for a more in-depth explanation of the SSL protocol.
See also below for: How do I know if my connection is secure?
What is Cryptography?
Cryptography is, in broad terms, the science of concealing data. Nowadays the term has come to mean something more precise. There are at least three approaches to concealing data:
A CODE is the substitution of a phrase for another phrase, so that "The bear wakes at midnight" could mean "advance by the western approach on the next signal". Codes are inflexible; only phrases which have previously been agreed on by both the sending and receiving parties can be transmitted.
Steganography is the concealment of one message within another, for example as the least-significant bits of a 32-bit bitmap file.
Ciphers are the substitution of one block of text by another according to some generally applicable rule. A simple cipher is "replace each letter by the letter after it": A becomes B, B becomes C and so on.
When people talk about cryptography, they usually mean the study and use of ciphers.
How do Ciphers Work?
Different ciphers work in different ways, but all (good) ciphers have the following things in common:
Their input and output are treated as byte streams.
To encrypt the data (to make it unreadable), we use the cipher with a key.
The exact form of the key depends on the cipher. Frequently, it can be a simple random number.
To decrypt the data (to make it readable again), we use the cipher with a key.
Ciphers are divided into asymmetric and symmetric ciphers on the basis of whether they use the same key to encrypt and decrypt (symmetric ciphers) or two different keys for the two processes (asymmetric ciphers).
Asymmetric ciphers have the advantage that one of the keys (the encryption key) can be made public. So long as you keep the decryption key private, you can send the encryption key to anyone you want. Only you will be able to read messages encrypted with the encryption key. For this reason people usually refer to the encryption key for an asymmetric cipher as the public key, and the decryption key as the private key.
This also provides a means of proving your identity. You encrypt a known message with your private key and send it to a friend. If your friend can decrypt the message correctly using the public key the message must have come from you. This idea forms the basis of digital signatures. Well-known asymmetric ciphers include RSA, Diffie-Hellman, DSA and forms of Elliptic Curve Cryptography.
Symmetric ciphers have the advantage of speed; they are frequently 100-1000 times faster than typical asymmetric ciphers in software. This makes them the cipher of choice when you are encrypting files for local storage.
If you want to send a secure message to someone else, you must find a way of transmitting the key securely. Well-known symmetric ciphers include DES, Triple DES, RC2, RC4and IDEA. The strength of a symmetric cipher is roughly measured by its key length. A 40 bit key is considered to be weak, whereas a 128 bit key is strong.
What is the SSL Protocol?
The SSL protocol was originally developed by Netscape Communications Corporation. The SSL protocol evolved to version 3.0 which has not been altered since November 1996, so it can be considered fairly stable. SSL has since evolved into the IETF TLS 1.0 protocol (for compatibility reasons, known as SSL 3.1), standardized as IETF RFC (Request for Comments) 2246 The TLS Protocol Version 1.0, dated January 1999.
How do I know if my connection is secure?
After your connection to the host has been established, check the left lower corner of the status bar. You will see either this icon for a
Secure SSL or TLS Connection
or the following one for a
Non SSL or TLS Connection
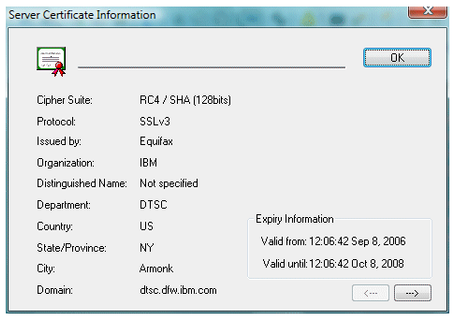
The first one indicates that you have an SSL or TLS connection, the second means your connection is not secure. To view additional details about a secure connection (Server certificate information and cipher strength), double-click on the icon in the status bar to display the following dialog: